Your Aws iam policy examples images are available. Aws iam policy examples are a topic that is being searched for and liked by netizens today. You can Download the Aws iam policy examples files here. Get all free vectors.
If you’re looking for aws iam policy examples images information linked to the aws iam policy examples interest, you have pay a visit to the right site. Our website always provides you with hints for seeking the highest quality video and picture content, please kindly hunt and locate more enlightening video articles and graphics that fit your interests.
Aws Iam Policy Examples. This example shows how you might create a policy that allows IAM users to view the inline and managed policies that are attached to their user identity. By Cezary Czekalski posted 18082021. Identity vs Resource-based AWS IAM Policies. See Who Has Access to Servers Storage Databases Running on AWS.
 How To Use Resource Based Policies In The Aws Secrets Manager Console To Securely Access Secrets Across Aws Accounts Aws Security Blog From aws.amazon.com
How To Use Resource Based Policies In The Aws Secrets Manager Console To Securely Access Secrets Across Aws Accounts Aws Security Blog From aws.amazon.com
AWS Identity and Access Management IAM recently launched managed policies which enable you to attach a single access control policy to multiple entities IAM users. These policies are created in Security Identity Identity Access Management Create Policy in the AWS. The awsuserid global condition key checks if the Unique ID of the principal making the request matches the Unique ID specified in the IAM policy. Launch Your Project On the Most Comprehensive Broadly Adopted Cloud Platform. Since it it contains both and it. The identity based policy is the one which can be attached directly with AWS identities like user group or a role.
Identity-based policies include AWS managed policies customer.
The identity based policy is the one which can be attached directly with AWS identities like user group or a role. Add an existing IAM managed policy to a new IAM role. The following example for Amazon QuickSight Enterprise and Standard editions shows a policy that you can use to enable a user to manage access to AWS resources. IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. The identity based policy is the one which can be attached directly with AWS identities like user group or a role. In order to create IAM policies in AWS CDK.
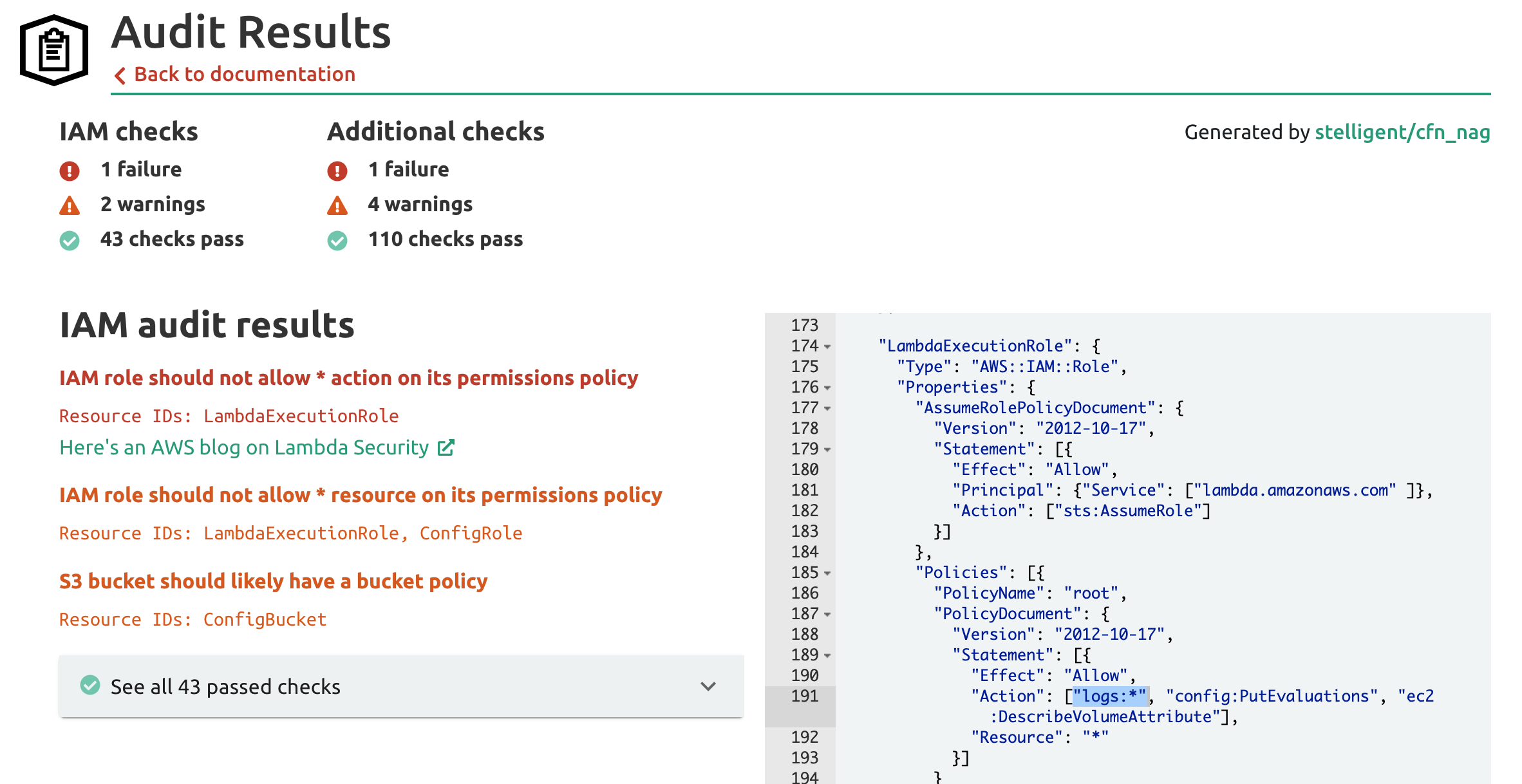
The identity-based policy is the one that can be attached directly with AWS identities like user group or a role. Deny-based service control policies can unintentionally limit or block your use of AWS services unless you add the necessary exceptions to the policy. The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. In this example you want to grant an IAM user in your AWS account access to one of your buckets awsexamplebucket1 and allow the.
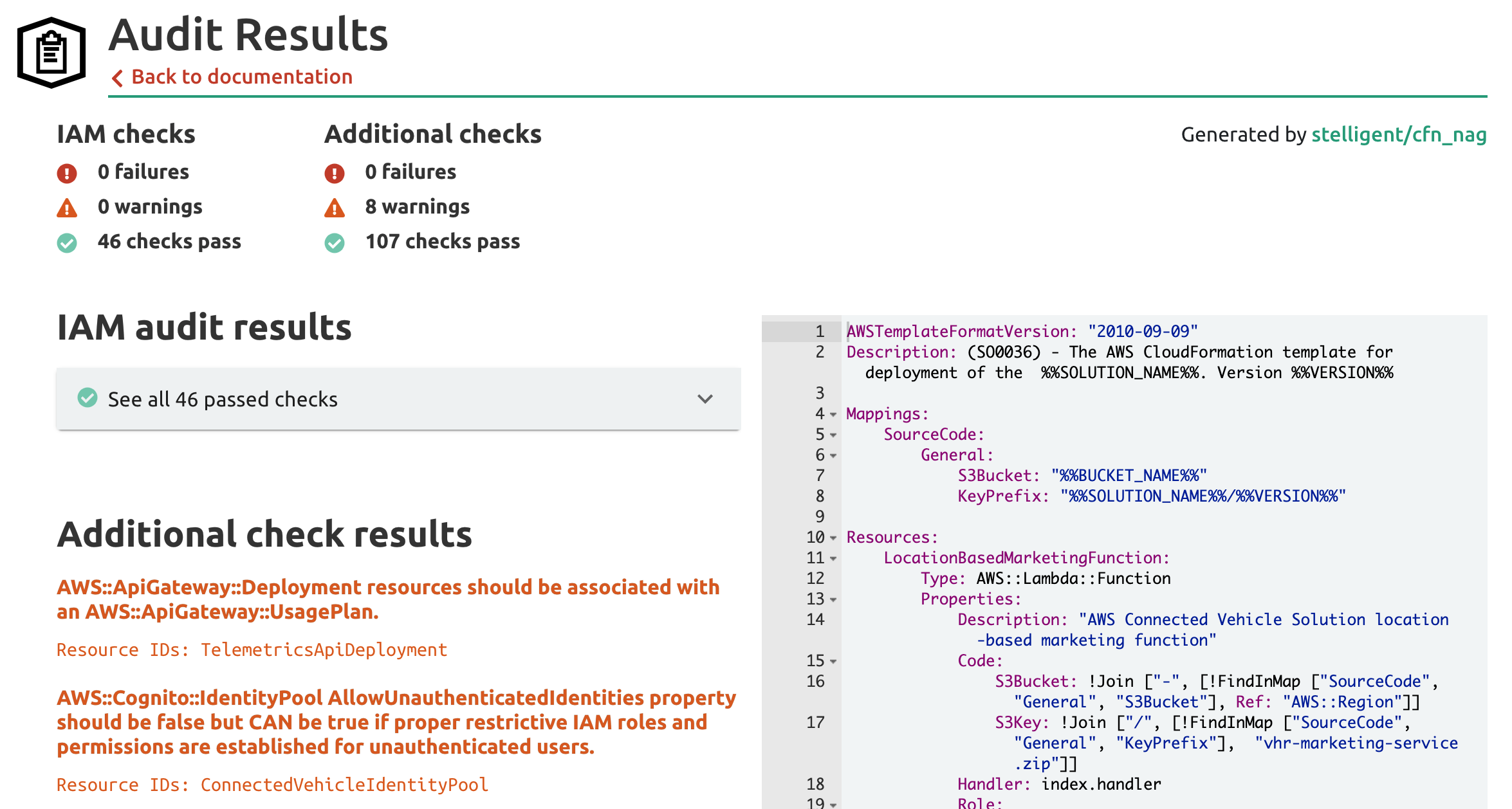
See Who Has Access to Servers Storage Databases Running on AWS. This is an optional step. Ad Automate AWS Access Provisioning Monitor for Inappropriate Unauthorized Unused Access. See Who Has Access to Servers Storage Databases Running on AWS. Ad Sign Up For an Account Get Free Hands-On Experience with 60 AWS Products.
 Source: sqlshack.com
Source: sqlshack.com
Ad Automate AWS Access Provisioning Monitor for Inappropriate Unauthorized Unused Access. See Who Has Access to Servers Storage Databases Running on AWS. Ad Automate AWS Access Provisioning Monitor for Inappropriate Unauthorized Unused Access. Ad Sign Up For an Account Get Free Hands-On Experience with 60 AWS Products. Ad Sign Up For an Account Get Free Hands-On Experience with 60 AWS Products.
 Source: aws.amazon.com
Source: aws.amazon.com
Adds or updates an inline policy document that is embedded in the specified IAM user group or role. Allowing an IAM user access to one of your buckets. Add an existing IAM managed policy to a new IAM role. Deny-based service control policies can unintentionally limit or block your use of AWS services unless you add the necessary exceptions to the policy. IAM policy is an example of that.
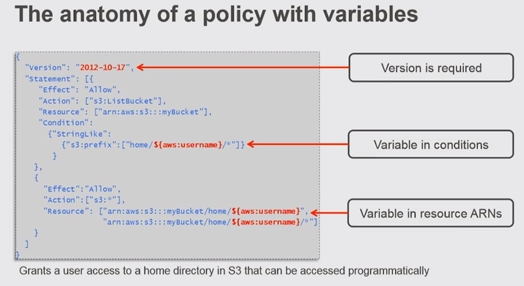 Source: bogotobogo.com
Source: bogotobogo.com
In the search box put the term. Since it it contains both and it. For example if you want to. The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. Deny-based service control policies can unintentionally limit or block your use of AWS services unless you add the necessary exceptions to the policy.
 Source: trendmicro.awsworkshop.io
Source: trendmicro.awsworkshop.io
AWS Identity and Access Management IAM recently launched managed policies which enable you to attach a single access control policy to multiple entities IAM users. Launch Your Project On the Most Comprehensive Broadly Adopted Cloud Platform. IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. This example shows how you might create a policy that allows IAM users to view the inline and managed policies that are attached to their user identity. Identity and Access Management IAM is a global AWS service dedicated to.
 Source: sqlshack.com
Source: sqlshack.com
The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. These policies are created in Security Identity Identity Access Management Create Policy in the AWS. The following are sample IAM policies with typical permissions configurations. You may want to rename this gist from AWS S3 bucket policy recipes. Identity and Access Management IAM is a global AWS service dedicated to.
 Source:
Source:
Identity and Access Management IAM is a global AWS service dedicated to. The following are sample IAM policies with typical permissions configurations. Add an existing IAM managed policy to a new IAM role. Identity vs Resource-based AWS IAM Policies. The identity-based policy is the one that can be attached directly with AWS identities like user group or a role.
 Source: cloudacademy.com
Source: cloudacademy.com
The identity-based policy is the one that can be attached directly with AWS identities like user group or a role. Allowing an IAM user access to one of your buckets. AWS Policies are of two kinds. To something like AWS S3 bucket policy and IAM policy recipes. Since it it contains both and it.
 Source: summitroute.com
Source: summitroute.com
To something like AWS S3 bucket policy and IAM policy recipes. In the search box put the term. IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. The following sections describe how to start using IAM including how to secure an AWS account create IAM users groups and policies and how to prepare for future growth and change in. Identity and Access Management IAM is a global AWS service dedicated to.
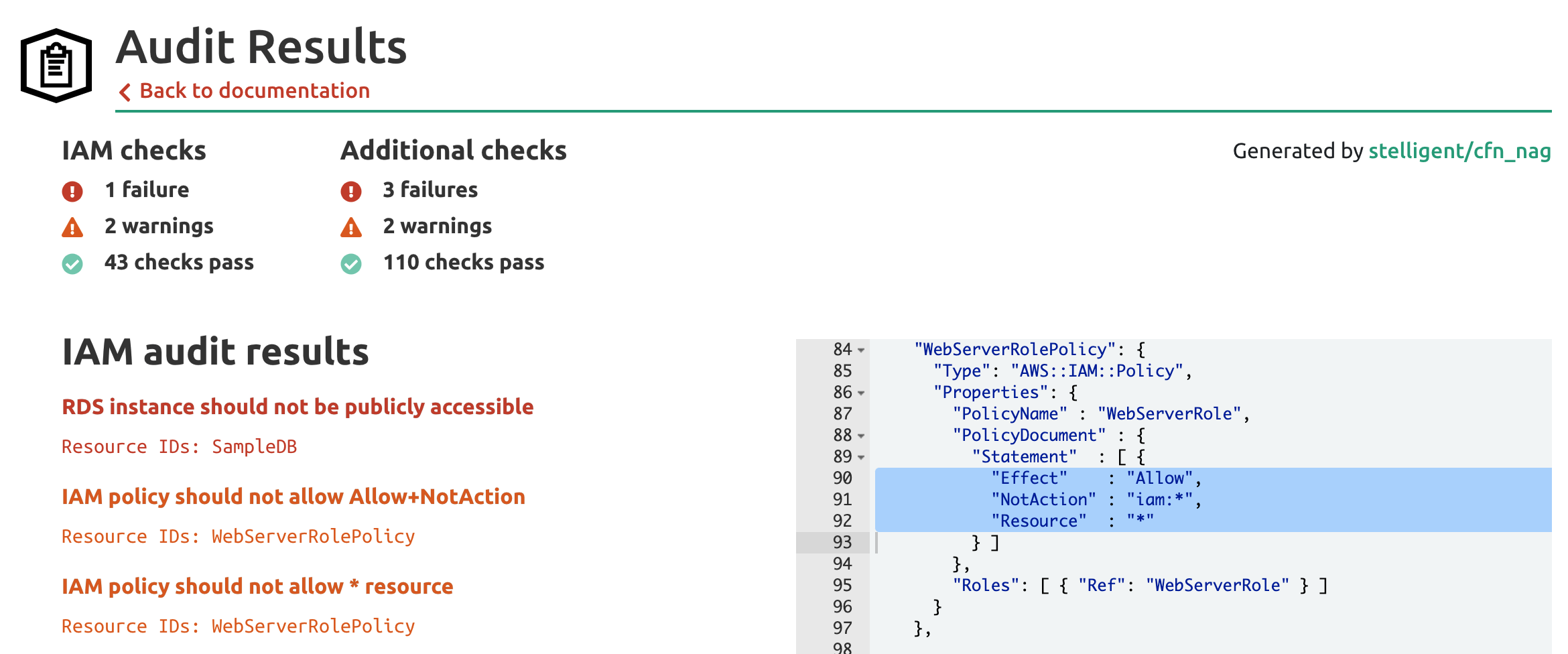
For an example of such an exception. Launch Your Project On the Most Comprehensive Broadly Adopted Cloud Platform. The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. Deny-based service control policies can unintentionally limit or block your use of AWS services unless you add the necessary exceptions to the policy. See Who Has Access to Servers Storage Databases Running on AWS.
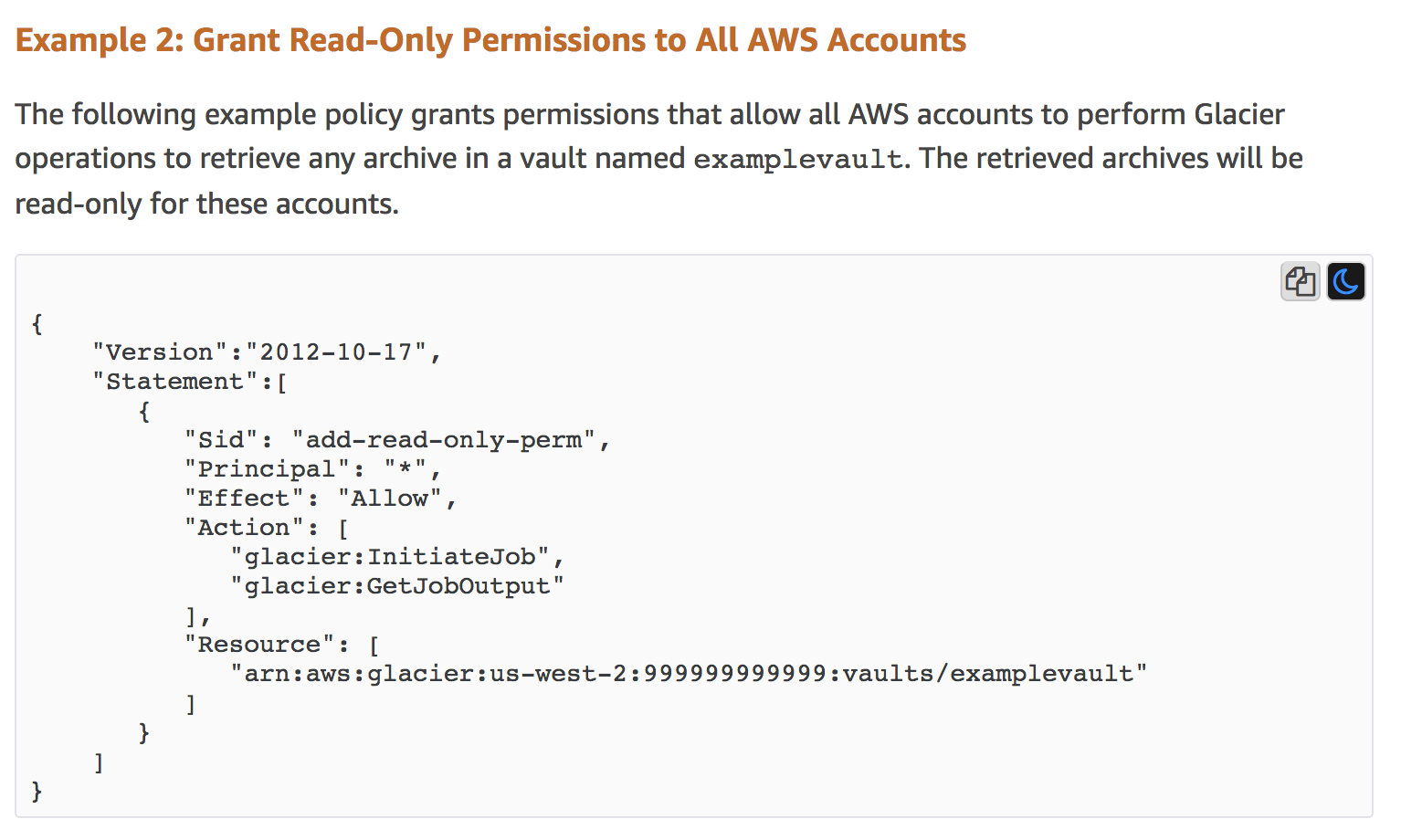 Source: summitroute.com
Source: summitroute.com
The identity based policy is the one which can be attached directly with AWS identities like user group or a role. By Cezary Czekalski posted 18082021. IAM policy is an example of that. The identity-based policy is the one that can be attached directly with AWS identities like user group or a role. See Who Has Access to Servers Storage Databases Running on AWS.
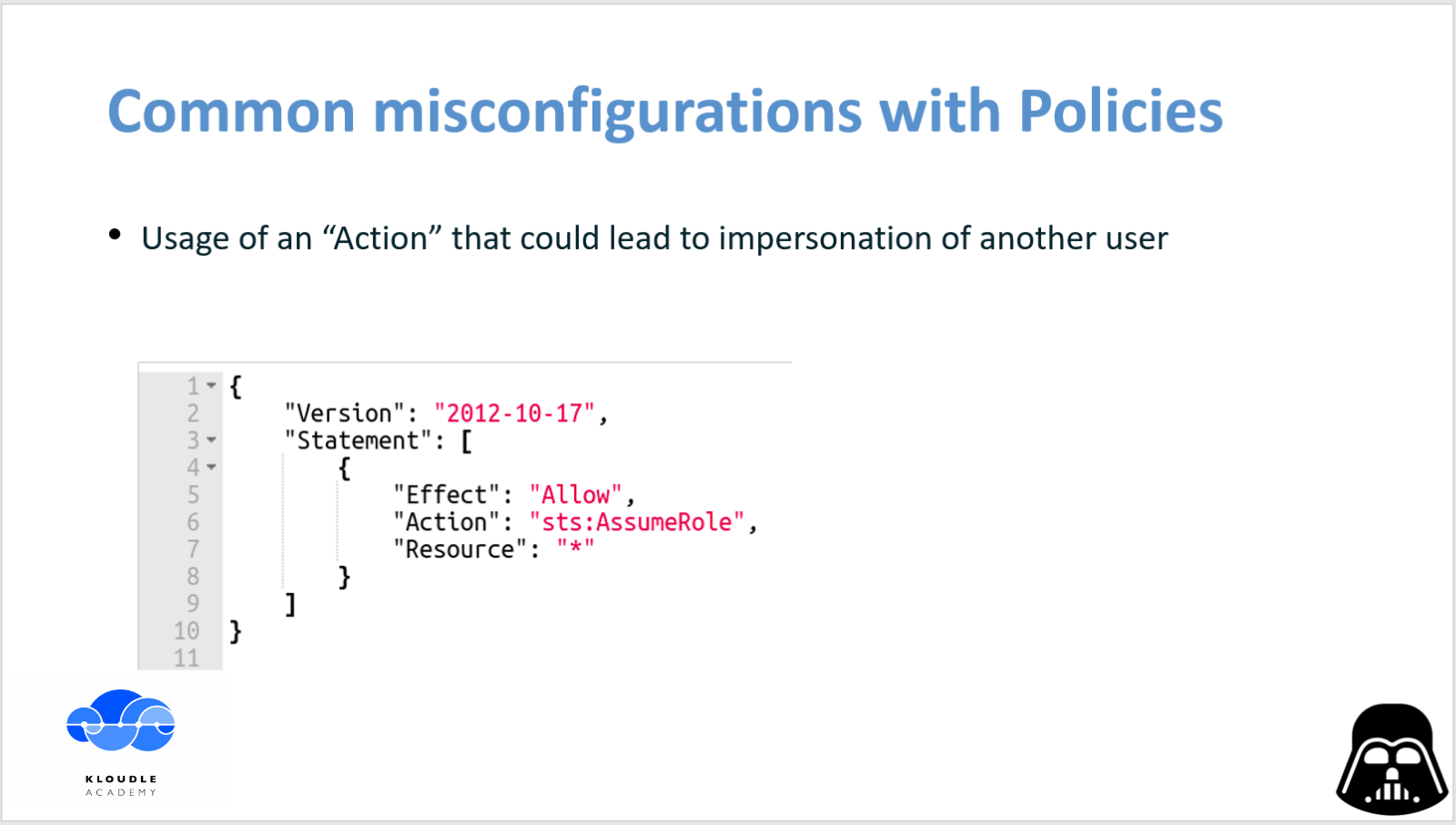 Source: kloudle.com
Source: kloudle.com
The following sections describe how to start using IAM including how to secure an AWS account create IAM users groups and policies and how to prepare for future growth and change in. The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. IAM policy is an example of that. Identity vs Resource-based AWS IAM Policies. Lets look at a few more examples to explore how broad.
 Source: aws.amazon.com
Source: aws.amazon.com
In my last post we looked at the structure of AWS IAM policies and looked at an example of a policy that was too broad. Allowing an IAM user access to one of your buckets. This is an optional step. For example if you want to. The following are sample IAM policies with typical permissions configurations.
 Source: cloudacademy.com
Source: cloudacademy.com
The following sections describe how to start using IAM including how to secure an AWS account create IAM users groups and policies and how to prepare for future growth and change in. Since it it contains both and it. IAM policy is an example of that. See Who Has Access to Servers Storage Databases Running on AWS. Allowing an IAM user access to one of your buckets.
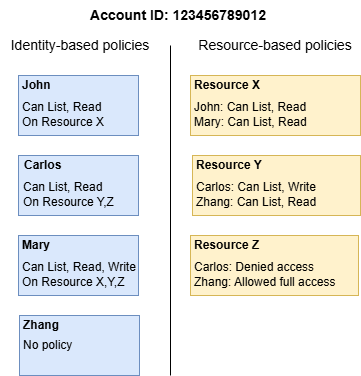 Source: docs.aws.amazon.com
Source: docs.aws.amazon.com
To something like AWS S3 bucket policy and IAM policy recipes. The policies specific to ElastiCache can be searched for by going to IAM dashboard selecting the policies section from the left tab. Adds or updates an inline policy document that is embedded in the specified IAM user group or role. IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. The awsuserid global condition key checks if the Unique ID of the principal making the request matches the Unique ID specified in the IAM policy.
 Source: docs.netapp.com
Source: docs.netapp.com
See Who Has Access to Servers Storage Databases Running on AWS. In my last post we looked at the structure of AWS IAM policies and looked at an example of a policy that was too broad. Most policies are stored in AWS as JSON documents that are attached to an IAM identity user group of users or role. Identity vs Resource-based AWS IAM Policies. In this example you want to grant an IAM user in your AWS account access to one of your buckets awsexamplebucket1 and allow the.
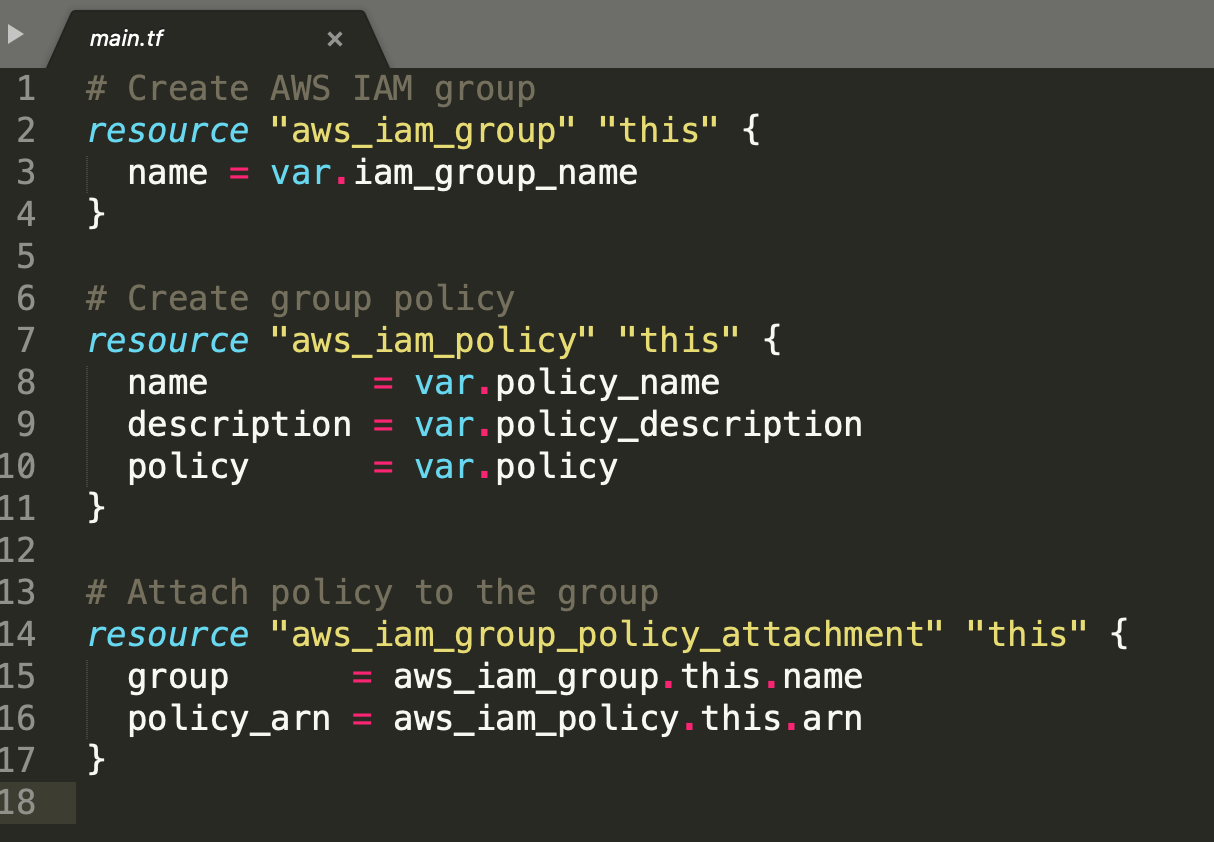 Source: cloudly.engineer
Source: cloudly.engineer
IAM Policies define specific permissions needed to access AWS resources and can be associated with IAM users roles or groups. Launch Your Project On the Most Comprehensive Broadly Adopted Cloud Platform. By Cezary Czekalski posted 18082021. Identity-based policies include AWS managed policies customer. Launch Your Project On the Most Comprehensive Broadly Adopted Cloud Platform.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title aws iam policy examples by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






